Synaptics announces in-display imprint sensor, coming to new phone from 'top five OEM'
Synaptics has reported mass produce of its Clear ID FS9500 optical in-display imprint sensors. The Clear ID in-display imprint sensors activate only the time needed and could be used with wet, dry, and cold fingers, tells Synaptics. The firm too tells which its Clear ID imprint sensors are twice as fast as three-dimensional facial recognition. Synaptics too tells which it'll offer private demos of its in-display imprint sensor on a "full-production, recently to be reported Tier one customer phone" at CES. Which device do you think going to be the premier to Utilize Synaptics' Clear ID in-display imprint sensor?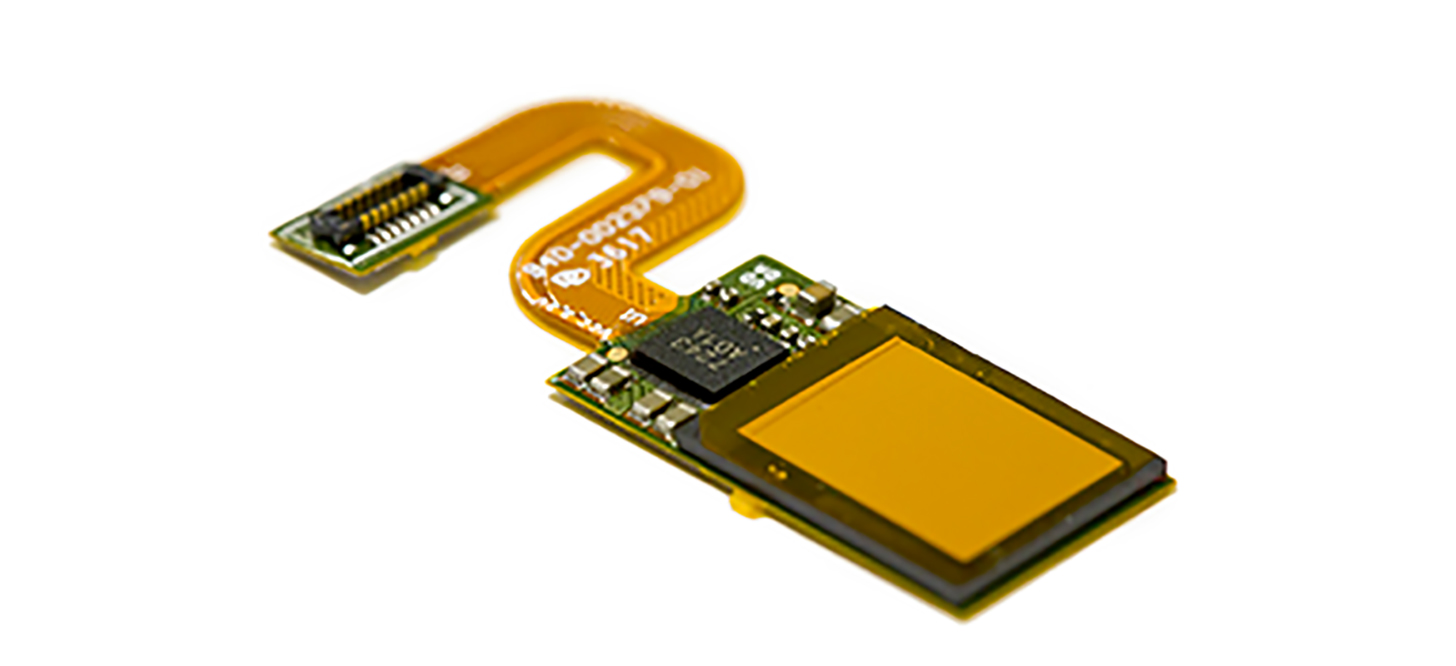
Tricks to speed up your old phone until you purchas a new one
as declared in Apple iPhones users could manage storage in Settings. iOS eleven could automatically uninstall applications that are rarely used, if the iPhone's storage is running low. They take up further space and if your smartphone's storage is endeed running low, it's likely to affect its performance too. Apple iPhones users could manage storage in Settings > General > iPhone Storage-> Manage storage. The other element that affects a smartphone's performance is the applications and processes running in the background.collected by :John Smith
Post a Comment